With the aws_security_group module, security groups (firewall rules) can be created using Terraform.
Each security group resource can define multiple ingress rules. Either by setting a single port or a port range:
resource "aws_security_group" "my_ec2_sg" {
name = "my-ec2-sg"
vpc_id = myvpcid
# Allow tcp 80 from ALB
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
security_groups = [aws_security_group.my_alb_sg.id]
}
# Allow tcp 6081+6082 from Mgmt
ingress {
description = "Allow Access to Varnish from Mgmt"
from_port = 6081
to_port = 6082
protocol = "tcp"
cidr_blocks = ["172.31.100.100/32"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
But when I needed to enable ICMP for monitoring, I had do dig a bit deeper.
ICMP is a different protocol than TCP or UDP, which are mostly used in data transmissions between applications. Besides being a different protocol, there's another major difference: ICMP doesn't use ports - instead different "code fields" are used to identify the ICMP type.
How can the ingress rule with port definition be "translated" to ICMP? What if I need all ICMP codes?
Let's ask AI. I prompted for an ingress rule allowing ICMP pings from a specific source. And AI (Grok) spit out the following ingress rule:
ingress {
description = "Allow ICMP ping from 172.31.100.100/32"
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["172.31.100.100/32"]
icmp_type = 8 # Echo Request (ping)
icmp_code = 0
}
To my untrained Terraform eyes this seems to look OK. Let's do a terraform plan and see how the security group would be altered...
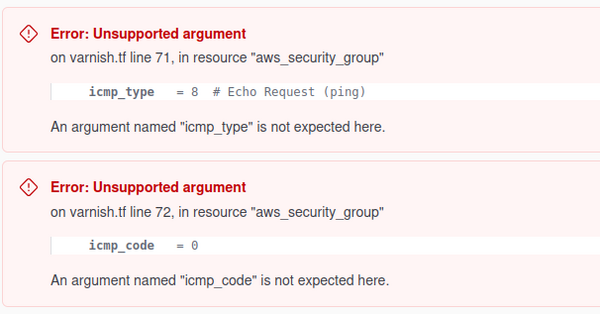
The plan failed!
An argument named "icmp_type" is not expected here.
An argument named "icmp_code" is not expected here.
The AI suggestion didn't work.
After digging deeper, with both AI and classical Search Engine research, the trick is to use the ingress ports as ICMP types/codes.This is also described in the aws_security_group module documentation:
from_port - (Required) Start port (or ICMP type number if protocol is icmp or icmpv6).
to_port - (Required) End range port (or ICMP code if protocol is icmp).
To allow all ICMP types from a specific source, you can use the following example:
ingress {
description = "Allow ICMP from Mgmt"
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["172.31.100.100/32"]
}
In the AWS Console, the ingress rule now shows "Port range All":
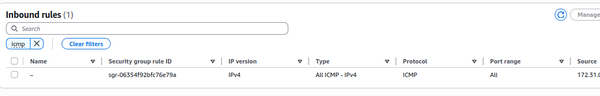
Pings and other ICMP codes, such as traceroute, are now working from the Mgmt machine.
Mike Anderson from Florida wrote on Sep 5th, 2025:
Your walkthrough is both practical and a gentle caution: verify AI output, especially when Terraform APIs don’t expect what we think they do. Really helpful post!

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder