I just had to solve a spamming issue on a shared hosting server, where a Joomla 1.5 (time to upgrade, eh?!) was hacked and used to upload several files, one of them a cgi web shell:
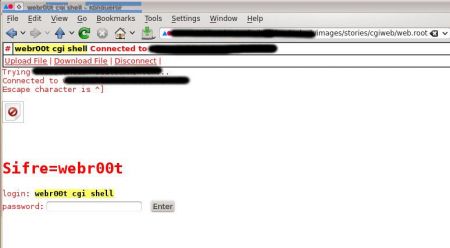
The interesting thing is, that this file extension doesn't end in ".cgi" or ".php", which makes it more difficult to automatic search mechanisms, which for example search for uploaded php files, to discover the file.
The hacker uploaded a .htaccess file into the cgiweb folder, declaring that the file extension ".root" should be used as cgi-script through AddHandler definition.
When the correct password was given, shell commands could be executed in the web shell, for example uname:
How to solve this? Well, a temporary solution is to delete the uploaded files and folders. But as old and end of life Joomla versions are and will stay vulnerable, the only real solution is that this web-customer upgrades his Joomla CMS.
No comments yet.

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder