Funny. Right after I posted the previous article (Uploaded and executed perl script through old Joomla vulnerability), I was informed about a hacked customer website on a FreeBSD web server and was asked for help to find out how this happened.
The customer's website didn't really look like a real website anymore. The hackers enjoyed to design their own little welcome page (and even embedded some background sound through a Youtube embed code):
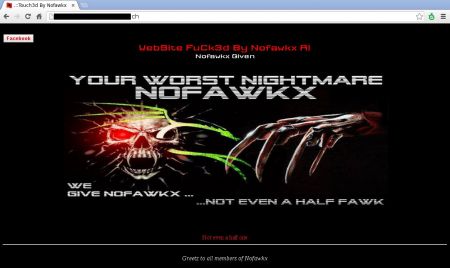
A quick look into the htdocs folder revealed a recent hack:
ls -ltr
total 21
[...]
-rw-rw-r-- 1 useraccount useraccount 3033 Nov 27 11:34 index.php
drwxrwxr-x 4 useraccount useraccount 8 Feb 8 01:08 userfiles
-rw-r--r-- 1 useraccount useraccount 8079 Feb 8 01:09 al.htm
So February 8th in the early mornings... By going through the access logs from that day, I quickly found the source IP (82.114.70.18) which was responsible for the hack.
The following POST on a tiny_mce script allowed the hacker to do an upload:
82.114.70.18 - - [08/Feb/2014:01:08:45 +0100] "POST /bcms/jscripts/tiny_mce/plugins/smexplorer/index.php?get=5caebac50093f182648b0b9a4c8a6a2fa259e541c69b9836c1a85e94ca35dba8b9e745d659c84c67d7e452caf31354f96d11333adcb95286d9e8c1c0a087c28de751ff236bb2981b44f3229454497d69f4fb9f6c5a5fbfed668ce3504ae41f366f338d1707712e7f0a38119a0e2e6fba416edb2f9c88ceea12e2bfa6bbe4714a18e7515a7beda94315baf3fb6b9c4663205ece4866728202bf9163ddb65db106673767377a0119a93289592dd90002d155025537e56ab386f259a2b69d262669054050875e1c768f3d7e945ed6617d86313007505d0081464f0563d2618258812e895537f8d2a5804b42c97b398bb0c1a45b33358d614fbdde4bf7816a8da3ada811e4afc09b0a770effdbe1520b09e23cac2b6ac630edbd495d34fc8a086c94e77792af8c0af2ecc981fe8483923ea6bf2484960e2cd2e87f&action=upload HTTP/1.1" 200 30572 "http://www.example.com/bcms/jscripts/tiny_mce/plugins/smexplorer/index.php?get=5caebac60093f182648b0b9a4c8a6a2fa259e541c69b9836c1a84998ca7e91aff7ea43c4409e063b8fb55681f2045cea2210332bdef518dbcbf6d8c3a489c380f04aea3337a7954f52f223ce7c536169fee89a245253a5af7096ee5e28b71c326f25b64c593b25681c020e9d196662ba416edb2f9c88c8ea13d8a09cb8f4221949bf19424cf6bf6e14b6eba312994a69310691316c74800d85973f89b951a15f5d3b5425610859ae3789583a8a790cd75d02552b872ab283f349bea8a76875780b404bbc580626c6312ad64fc3634d813c03044d481590021913369b63ad578622826e6ca198b5834e57cd22408eb1c8a24415368d2f1aa1c149c7966fa0aca5a618f2fb9c9a583218fadbec4d0b08e820ab7f" "Mozilla/5.0 (Windows NT 6.1; rv:27.0) Gecko/20100101 Firefox/27.0"
Through that POST, a new file (wso.2.5.1.php) was uploaded. As I've seen a lot of hacks in the past years, I already knew that this will be a WSO PHP Shell.
Optical verification:
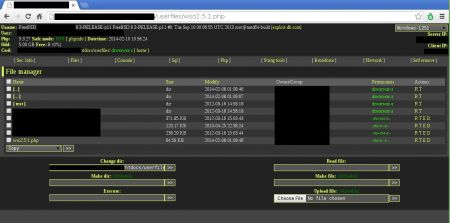
Right after the upload of the web shell, it was executed several times:
82.114.70.18 - - [08/Feb/2014:01:08:49 +0100] "GET /userfiles/wso2.5.1.php HTTP/1.1" 200 13929 "http://www.example.com/bcms/jscripts/tiny_mce/plugins/smexplorer/index.php?get=5caebac50093f182648b0b9a4c8a6a2fa259e541c69b9836c1a85e94ca35dba8b9e745d659c84c67d7e452caf31354f96d11333adcb95286d9e8c1c0a087c28de751ff236bb2981b44f3229454497d69f4fb9f6c5a5fbfed668ce3504ae41f366f338d1707712e7f0a38119a0e2e6fba416edb2f9c88ceea12e2bfa6bbe4714a18e7515a7beda94315baf3fb6b9c4663205ece4866728202bf9163ddb65db106673767377a0119a93289592dd90002d155025537e56ab386f259a2b69d262669054050875e1c768f3d7e945ed6617d86313007505d0081464f0563d2618258812e895537f8d2a5804b42c97b398bb0c1a45b33358d614fbdde4bf7816a8da3ada811e4afc09b0a770effdbe1520b09e23cac2b6ac630edbd495d34fc8a086c94e77792af8c0af2ecc981fe8483923ea6bf2484960e2cd2e87f&action=upload" "Mozilla/5.0 (Windows NT 6.1; rv:27.0) Gecko/20100101 Firefox/27.0"
82.114.70.18 - - [08/Feb/2014:01:08:51 +0100] "POST /userfiles/wso2.5.1.php HTTP/1.1" 200 14966 "http://www.example.com/userfiles/wso2.5.1.php" "Mozilla/5.0 (Windows NT 6.1; rv:27.0) Gecko/20100101 Firefox/27.0"
82.114.70.18 - - [08/Feb/2014:01:08:56 +0100] "POST /userfiles/wso2.5.1.php HTTP/1.1" 200 14966 "http://www.example.com/userfiles/wso2.5.1.php" "Mozilla/5.0 (Windows NT 6.1; rv:27.0) Gecko/20100101 Firefox/27.0"
82.114.70.18 - - [08/Feb/2014:01:09:07 +0100] "POST /userfiles/wso2.5.1.php HTTP/1.1" 200 15593 "http://www.example.com/userfiles/wso2.5.1.php" "Mozilla/5.0 (Windows NT 6.1; rv:27.0) Gecko/20100101 Firefox/27.0"
The website's index.php was overwritten a few days later as stat revealed:
stat index.php
4230937973 41 -rw-rw-r-- 1 useraccount useraccount 4294967295 3033 "Feb 10 10:47:42 2014" "Nov 27 11:34:33 2013" "Feb 9 21:10:45 2014" "Feb 9 21:10:45 2014" 7168 5 0 index.php
Without big surprise it was once again the wso script which caused this change:
82.114.70.18 - - [09/Feb/2014:21:10:45 +0100] "POST /userfiles/wso2.5.1.php HTTP/1.1" 200 12342 "http://www.example.com/userfiles/wso2.5.1.php" "Mozilla/5.0 (Windows NT 6.1; rv:27.0) Gecko/20100101 Firefox/27.0"
One of the uploaded files from the hacker was called "al.htm" and contained a video with a message from the hacker.
The message was basically, that the website had "0 security".
Let's verify if the hacker was right by checking the version of the abused tiny_mce script:
more bcms/jscripts/tiny_mce/tiny_mce.js
var tinymce={majorVersion:'3',minorVersion:'0.6.2',releaseDate:'2008-04-07'
A tiny_mce script from 2008. Why am I not surprised?
No comments yet.

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder