It's been quite some time since I wrote a post about a web-hack. Honestly, they mostly look the same and I usually don't see any new tools. Until this week, when I came across another kind of php web shell (for once not a WSO Shell).
It all started with the typical findings of a hack. Sub-processes were launched by the user www-data, which means the Apache user.
After some investigation, the responsible virtual host was quickly identified. The sub-processes (which were trying to send spams) were launched by a script:
201.123.70.188 - - [07/Oct/2015:08:00:39 +0200] "POST /wp-includes/images/maiBOUBA.php HTTP/1.1" 200 18014 "http://www.example.com/wp-includes/images/maiBOUBA.php" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
Of course I wanted to check out what kind of script this is and I visited the URL. Turns out, the script maiBOUBA.php is a Priv8 mail form:
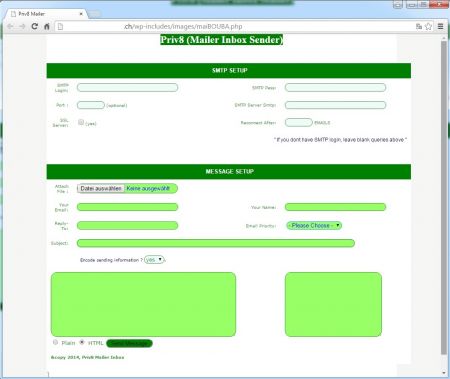
So yes, this is typically used by spammers. But how did it get on the server? The file itself was created a few hours before the spamming started:
stat maiBOUBA.php
File: `maiBOUBA.php'
Size: 106758 Blocks: 224 IO Block: 4096 regular file
Device: fd01h/64769d Inode: 5932234 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 33/www-data) Gid: ( 33/www-data)
Access: 2015-10-07 00:04:23.000000000 +0200
Modify: 2015-10-07 00:03:58.000000000 +0200
Change: 2015-10-07 00:03:58.000000000 +0200
Around that time there were a lot of requests with strange parameters in the access log:
201.123.70.130 - - [07/Oct/2015:00:03:40 +0200] "GET /lndex.php?x=img&img=arrow_ltr HTTP/1.1" 200 88 "http://www.example.com/lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
201.123.70.130 - - [07/Oct/2015:00:03:57 +0200] "POST /lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a HTTP/1.1" 200 5214 "http://www.example.com/lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
201.123.70.130 - - [07/Oct/2015:00:03:59 +0200] "GET /lndex.php?x=img&img=sort_asc HTTP/1.1" 200 85 "http://www.example.com/lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
201.123.70.130 - - [07/Oct/2015:00:03:59 +0200] "GET /lndex.php?x=img&img=ext_lnk HTTP/1.1" 200 572 "http://www.example.com/lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
201.123.70.130 - - [07/Oct/2015:00:03:59 +0200] "GET /lndex.php?x=img&img=ext_png HTTP/1.1" 200 175 "http://www.example.com/lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
201.123.70.130 - - [07/Oct/2015:00:03:59 +0200] "GET /lndex.php?x=img&img=change HTTP/1.1" 200 290 "http://www.example.com/lndex.php?x=ls&d=%2Fvar%2Fwww%2Fweb173%2Fhtml%2Fwp-includes%2Fimages&sort=0a" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0"
My first thought was that the Wordpress version is so old that a vulnerability was abused. But only at the third look at the access log something has hit my eye: The requested URI was lndex.php (with an L), not index.php.
I verified this and indeed, there was a file in the document root called "lndex.php":
stat lndex.php
File: `lndex.php'
Size: 132410 Blocks: 272 IO Block: 4096 regular file
Device: fd01h/64769d Inode: 5915121 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1973/ web173) Gid: ( 1973/ web173)
Access: 2015-10-06 23:53:24.000000000 +0200
Modify: 2015-10-06 23:49:36.000000000 +0200
Change: 2015-10-06 23:49:36.000000000 +0200
The top of the file even contained a password in cleartext, how to access the file (wow, for once not an encrypted password - that's rare):
@session_start();
@set_time_limit(0);
#####cfg#####
# use password true / false #
$create_password = true;
$password = "hardwork";
######ver####
$ver= "v1.3";
#############
@$pass=$_POST['pass'];
if($pass==$password){
$_SESSION['nst']="$pass";
With this information I checked lndex.php out and surprise, a new kind of php web shell appears. This one is called fx() and is kind of similar to WSO but contains some other functions.
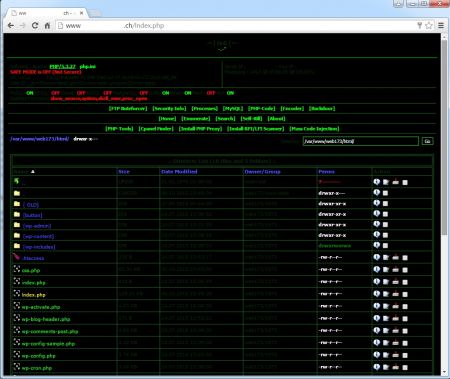
OK now that it is clear, that this web shell was used to upload additional files and to start sub-processes (by having uploaded and executed perl scripts), how did this file get on the server?
I expected to find hints of a Wordpress vulnerability in the access logs, but instead it turns out the file was uploaded by FTP (as seen in the ftp servers transfer logs):
Tue Oct 06 23:45:03 2015 1 114.79.33.248 66907 /var/www/web173/html/css.php a _ i r web173 ftps 0 * c
Tue Oct 06 23:49:36 2015 0 78.47.143.141 132410 /var/www/web173/html/lndex.php a _ i r web173 ftp 0 * c
So for once the source of the hack was not a Wordpress vulnerability but rather a (most likely) insecure password.
No comments yet.

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder