Yesterday I successfully installed NagVis 1.8 with Icinga 2 as backend. I started to create the first maps and was about to send the link to the first colleagues - until I realized that I should fix the login.
By default NagVis uses its own sqlite database for authentication. Which means that I'd have to create a new user for each colleague. That's OK for up to 5 users, but not if we're talking about potential 50-100 users...
Icinga 2 itself is already configured to use the company's Active Directory via LDAP as authentication mechanism. I wanted to do the same with NagVis. However once authenticated, the user should automatically have a read-only view on the public maps. Unfortunately there is not a lot of documentation how to achieve this, but after some try'n'err, I finally got it working.
One note before you begin: Make sure you are logged into the NagVis interface as admin! Do not log out.
In the NagVis config file (nagvis.ini.php), there are several logon modules (LogonMixed, LogonEnv, LogonMultisite) which can be chosen. Just below the comments where the different modules are explained, I added the following config:
logonmodule="LogonMixed"
logonenvvar="REMOTE_USER"
logonenvcreateuser="1"
logonenvcreaterole="Guests"
NagVis will now use the LogonMixed module. This means that NagVis will use the Apache environment variable "REMOTE_USER" (see second line) as the username to handle. If the REMOTE_USER variable is empty it will fall back to the NagVis logon prompt.
The logonenvcreateuser option set to 1 tells NagVis to automatically create the user (once again read from the REMOTE_USER variable submitted by the browser) in the NagVis user db if it doesn't exist.
And at the end NagVis is told to automatically assign the role "Guests" to the newly created users.
Now the Apache configuration for NagVis needs to be modified. In my case this is the file /etc/apache2/conf-enabled/nagvis.conf (which is a symlink to /etc/apache2/conf-available/nagvis.conf). Right after the
Alias /nagvis "/srv/nagvis/share"
Options FollowSymLinks
AllowOverride All
[...]
This will allow a .htaccess file to override settings, like authentication mechanism.
And exactly this .htaccess file is now created in the NagVis share folder (/srv/nagvis/share/.htaccess):
# cat /srv/nagvis/share/.htaccess
AuthName "NagVis Access"
AuthType Basic
AuthBasicProvider file ldap
AuthUserFile /etc/icinga2-classicui/htpasswd.users
Require valid-user
AuthLDAPURL "ldap://dc01.example.com dc02.example.com/dc=example,dc=com?sAMAccountName"
AuthLDAPBindDN "CN=Service Account Icinga,OU=Service Accounts,OU=Users,DC=example,DC=com"
AuthLDAPBindPassword "secret"
This is the exact same authentication configuration I already use for Icinga Classic UI. When the user now accesses the NagVis URL, the typical authentication window will pop up:
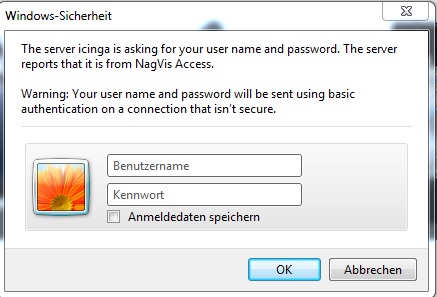
The user can log in with his Active Directory credentials and is then able to see all the maps to which the role "Guests" has access to.
Remember that you're still logged in as admin? Now you are able to see the automatically created users in "User menu" -> "Manage Users":
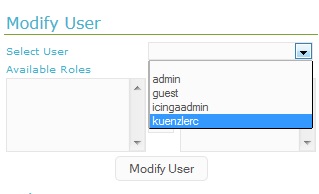
Hurray! My personal AD user (kuenzlerc) was added. Because I'm still logged in as admin, I can now assign the role "Administrators" to my personal AD user. And you can start assigning roles to other AD users, too.
ck from Switzerland wrote on Jan 24th, 2017:
AmbroAnalog, you can create the file with the htpasswd (or htpasswd2) command.
AmbroAnalog from Germany wrote on Jan 24th, 2017:
In my installation of Icinga I dont finde the File AuthUserFile /etc/icinga2-classicui/htpasswd.users
What can I do?
ck from Switzerland wrote on Oct 26th, 2016:
Hi Mike. Yes, the ldap module is required. I already had this module enabled on my Apache installation because I also make the login to Icinga with LDAP users. Here are the modules enabled on that server:
# ls /etc/apache2/mods-enabled/
access_compat.load authn_file.load autoindex.conf deflate.conf filter.load mpm_prefork.conf php5.load
alias.conf authnz_ldap.load autoindex.load deflate.load ldap.conf mpm_prefork.load setenvif.conf
alias.load authz_core.load cgid.conf dir.conf ldap.load negotiation.conf setenvif.load
auth_basic.load authz_host.load cgid.load dir.load mime.conf negotiation.load status.conf
authn_core.load authz_user.load cgi.load env.load mime.load php5.conf status.load
Mike from Aurora CO wrote on Oct 25th, 2016:
Claudio,
Did you need any packages not listed here for this to work, i.e. mod_auth_ldap?
I followed these steps but entering a valid Domain Controller user/pwd in the NagVis login page results in a failure.
Please advice.
Thanks!
Mike

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder