Although there's not much news about Checkpoint firewalls in recent years, that doesn't mean this isn't used in (mostly larger) companies anymore.
Checkpoint firewalls can perfectly be monitored using SNMP, as I already wrote in older posts:
I mostly get called in for monitoring related issues on Checkpoint firewalls after an update is installed. And this also what happened in this situation. After the Checkpoint VSX was upgraded from R81.10 to R81.20, the SNMP-based monitoring was not correctly working anymore.
For the monitoring of this Checkpoint VSX, including the virtual firewalls, the widely known and open source monitoring plugin check_nwc_health is used in the background of Icinga2.
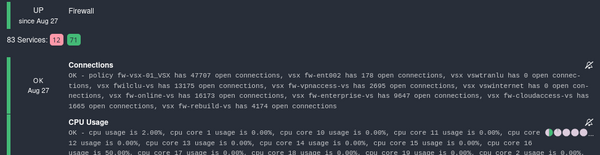
While the SNMP checks on the firewall device itself worked as expected, the checks on the virtual firewalls stopped working and ran into a timeout. The network interfaces from the virtual firewall instances (VS) did not respond to SNMP requests anymore.
It is important here to understand that a virtual firewall, identified by VSID, shows its interfaces (and other informational data) inside its own SNMP context. The name of the virtual firewall, for example vsid5, represents the SNMP context to use.
A manual verification of the plugin shows the same error message (timeout) as also shown in the Icinga2 user interface:
ck@icinga:~$ /usr/lib/nagios/plugins/check_nwc_health --hostname checkpoint1 --protocol 3 --username nagios --authpassword secret --authprotocol sha256 --contextname vsid5 --mode list-interfaces
UNKNOWN - check_nwc_health timed out after 15 seconds
Note: There's manual patching needed to enable sha256 as SNMP authentication protocol in Perl's Net::SNMP.
In order to access the SNMP context of a VS, direct access to it must be enabled. That was the case before - but maybe the Checkpoint upgrade did a configuration reset?
Once logged into the Checkpoint firewall device using SSH, the settings must be verified using the clish:
[Expert@vsx:0]# clish
vsx:0> show snmp vs-direct-access
off
The output shows the hard truth: The direct SNMP access to the|any VS (context) is not enabled.
To enable vs-direct-access, you must first switch to the "vs" SNMP mode, then set the option to on:
vsx:0> set snmp mode vs
vsx:0> set snmp vs-direct-access on
vsx:0> show snmp vs-direct-access
on
This should already be enough; the direct access to the SNMP contexts (VSID's) should now work.
Right after enabling vs-direct-access in the clish, the SNMP context of a virtual firewall (here vsid5) could be accessed again:
ck@icinga:~$ /usr/lib/nagios/plugins/check_nwc_health
--hostname checkpoint1 --protocol 3 --username nagios --authpassword
secret --authprotocol sha256 --contextname vsid5 --mode list-interfaces
000001 lo
000002 gre0
000003 gretap0
000004 br5
000027 wrpj513
000029 wrpj577
000031 wrpj385
000039 wrpj451
000041 wrpj192
000094 bond1.500
OK - have fun
A couple of minutes later, all interface checks of the virtual firewalls started to turn green again in Icinga2.
No comments yet.

AWS Android Ansible Apache Apple Atlassian BSD Backup Bash Bluecoat CMS Chef Cloud Coding Consul Containers CouchDB DB DNS Databases Docker ELK Elasticsearch Filebeat FreeBSD Galera Git GlusterFS Grafana Graphics HAProxy HTML Hacks Hardware Icinga Influx Internet Java KVM Kibana Kodi Kubernetes LVM LXC Linux Logstash Mac Macintosh Mail MariaDB Minio MongoDB Monitoring Multimedia MySQL NFS Nagios Network Nginx OSSEC OTRS Observability Office OpenSearch PHP Perl Personal PostgreSQL PowerDNS Proxmox Proxy Python Rancher Rant Redis Roundcube SSL Samba Seafile Security Shell SmartOS Solaris Surveillance Systemd TLS Tomcat Ubuntu Unix VMware Varnish Virtualization Windows Wireless Wordpress Wyse ZFS Zoneminder